The Office of Compliance Inspections and Examinations (“OCIE”) published a Risk Alert highlighting the need for investment advisers to prevent unauthorized access to client data stored on websites.
Recently, cyber attackers have used “credential stuffing” and other methods to breach web-based user accounts. Credential stuffing is when a hacker combines lists of stolen account information from the dark web and customized scripts to compromise user names and passwords to other sites. Hackers prefer this method because it seems to be more efficient and successful than more traditional methods of hacking, like a brute force attack.
OCIE has the following recommendations for Investment Advisers to consider in protecting themselves and their websites against credential stuffing attacks:
- Update password policies – Ensure that your firm’s password requirements are consistent with the requirements provided by the National Institute of Standards and Technology. It’s important to not re-use passwords used on other sites, as they may be compromised which leaves your password susceptible to a credential stuffing attack. If anyone at your firm or a client of your firm has an indication that their passwords have been compromised, it is a good idea to change them.
- Use multifactor authentication – The more factors your firm decides to implement in its security systems, the safer your firm’s data will be. The SEC recommends more than one additional factor because some hackers are able to access information that would help them bypass 2-factor authentication. Firms should be careful of text-based multifactor authentication as that security is only as good as the security on a given cell phone.
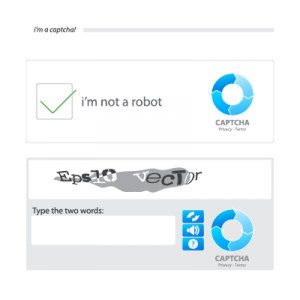
- Use CAPTCHA software – Completely Automated Public Turing test to tell Computers and Humans Apart (“CAPTCHA”) software is designed to prevent automated bots from accessing logins for sensitive data on a website. CAPTCHA requires a user to perform a test that is difficult to program an automated bot to pass. A common example of a CAPTCHA safeguard is typing a combination of letters from a displayed image:
- Implementing credential stuffing prevention software – There are various tools you can use to help monitor your firm’s systems. Some firms have implemented software which detects abnormal amounts of login attempts or abnormal amounts of failed login attempts to try to determine if a credential stuffing attack is taking place. Going further, some firms create virtual profiles of login attempts to their website which catalogue and classify as much information from the user as possible, such as operating system, IP address, language, browser, etc.
- Firewalls – A Web Application Firewall (“WAF”) is a firewall specifically designed for web use that can detect credential stuffing attacks. Once a WAF identifies that an attack is taking place, it has tools to limit access to information to prevent the attacker from accessing all of the firm’s data.
- Dark web monitoring – Some firms monitor the dark web to try to determine if their data has been compromised and is for sale on the dark web.
Firms should determine whether one or more of the above recommendations are necessary for security of data stored online. Firms should also consider whether they should communicate any message to firm clients to help them understand how to protect against various cyber threats.
Century Compliance, LLC, provides stand-alone phishing testing and cybersecurity training programs for investment advisers. If you require assistance with reviewing, updating, or drafting the policies and procedures required to have an effective cybersecurity compliance program, or are preparing to be examined by a regulator, please contact Parker MacIntyre or our affiliated compliance consulting firm, Century Compliance, LLC, at (678) 902-4060.
 RIA Compliance Blog
RIA Compliance Blog